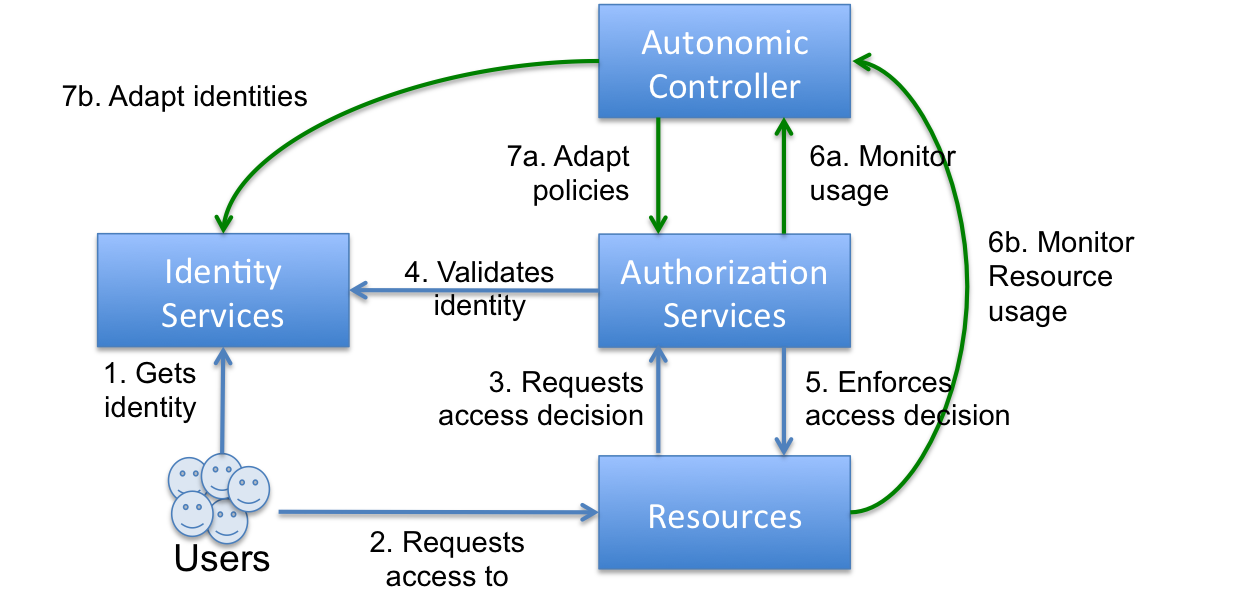
A self-adaptive authorization infrastructure, as shown in figure 3, is composed of all the components you would expect to see in an authorization infrastructure, yet with the addition of autonomic controllers, probes, and effectors.
Autonomic controllers realise a system's ability to self-adapt, and they are part of a feedback control loop which monitors and assesses a perceived state of the target authorization infrastructure. They provide the decision engine in which the authorization infrastructure is assessed for malicious behavior, and decide if action needs to be taken, and exactly what action should be taken.

Figure 3. Self-adaptive authorization infrastructure
Figure 4 exemplifies an autonomic controller based upon the MAPE-K loop (monitor, analyse, plan, and execute), whereby data collected by probes is utilized to produce a model of the system and its environment.Through the analysis of such models, we are able to detect system and/or environmental conditions that are consistent to malicious behaviour (a signature or anomaly based rule that indicates potential insider threat). The detection of malicious behavior within the system state triggers the selection of an ideal solution, one which prevents the behavior from reoccurring, whilst minimising unnecessary risk or impact to the target system's known user base.
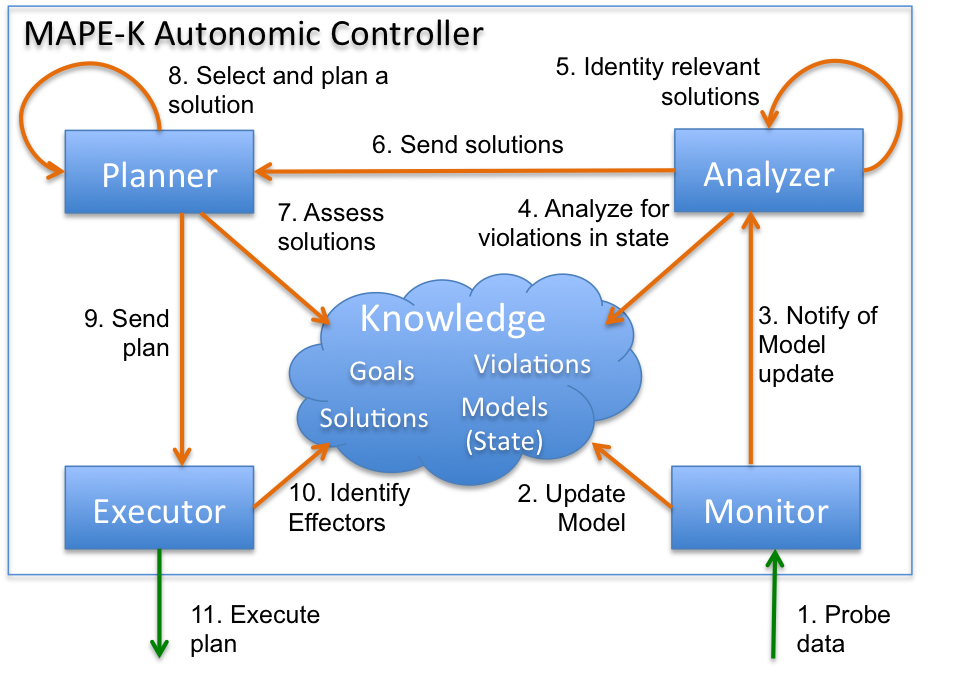
Figure 4. Autonomic controller conceptual design