A first step towards enabling adaptive authorization is to modelling the target domain in which adaptation should take place. It has allowed us to identify what can be monitored, and what can be controlled.
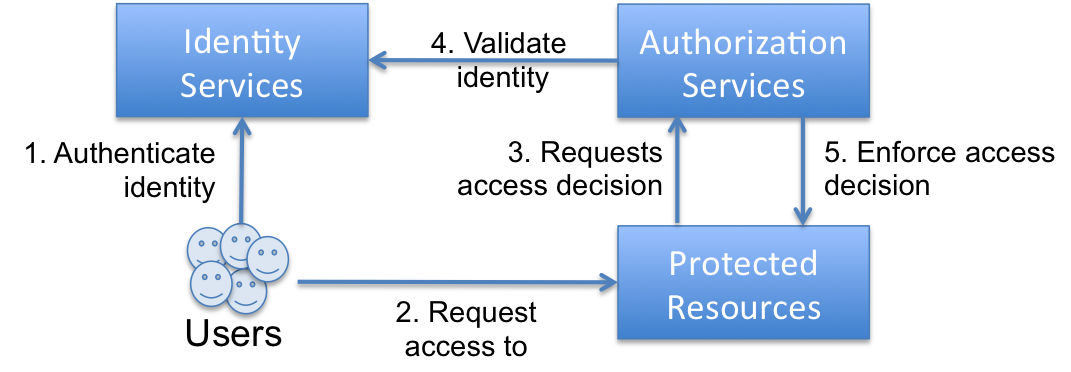
A simple domain model (figure 1) considers the abstract components of an authorization infrastructure. Typically, an authorization infrastructure consists of authorization services, identity services, protected resources, and users. An authorization service generates access control decisions based on a user's set of access rights. Identity services provide a means to authenticate users and maintain a user's set of access rights. Finally, protected resources rely on identity services and authorization services to ensure only authenticated and authorized users should gain access. Components of an authorization infrastructure may either exist as an integral part of bespoke systems or as separate systems in their own right. We do not distinguish between the two, rather that these components must exist to enable proper authorization.

Figure 1. A simple authorization infrastructure domain model
From figure 1, we can understand at a high level what kind of events take place, where we can observe those events, and what components we can adapt in order to control future events.
The simple domain model provides a basic understanding of core components of an authorization infrastructure. It is plausible to state that many authorization infrastructures will conform to this simple domain model, however for specific implementations of authorization/access control models we must expand. For example, figure 2 depicts a complex domain model for an ABAC (Attribute Based Access Control) federated authorization infrastructure, which considers types belonging to the access control model, along side architecture types.
Figure 2. ABAC federated authorization infrastructure domain model
Despite the complexity of figure 2, the benefit of detailing an authorization infrastructure in such a way allows us to identify the positioning of probes and effectors. Probes and effectors are critical to self-adaptive systems as they allow the collection of data about the state of the system, and the ability for a system to adapt itself. For example, a probe positioned at a PolicyDecisionPoint would enable the collection of data, portraying access requests and decisions. An effector positioned within an IdentityProvider would enable the adaptation of user access rights.